CDK Cyber Attack Why Do Cyber Attacks Seem So Widespread?
receive to our latest blog update where we investigate into the fascinating realm of popular photos such as DNSFilter: Assigning Cybersecurity Responsibility After a Cyberattack. In this era of image-based substance , remaining up-to-date with the recent trends can boost you relate with your readers and elevate your firm's participation .
Fashionable visuals are crucial for diverse reasons like 8 Reasons SMBs are a Top Target For Cyber Attacks - Network Doctor, Cyber Threats Part 2: Phishing and Spear Phishing Attacks - TSG. First , they attract the general's interest , bringing them significantly prone to be spread and favored . Furthermore , they portray the real-time sentiment and events , allowing your material to remain applicable . Ultimately , they deliver insights into that forms of images align most with individuals .
There are multiple applications and platforms to aid you discover trending images . Online networks locations like Gram , Tweet Space, and Pin It frequently present what has at this time popular . Markers can provide a excellent technique to follow current matters and associated graphics . Furthermore , platforms like Internet Search Analytics and BuzzSumo offer quantitative understanding .
Environmental Realization : Images illustrating climate alteration , eco-friendliness , and planet-friendly actions are exceedingly favored as a greater number of people transform into eco-consciously cognizant .
Vitality and Vitality: Visuals and visuals like 5 Signs a Cyberattack Is Under Way and 5 Things You Need to Do Before pertaining to training, cognitive well-being , and self-maintenance endure to expand as humans highlight their health . Tech : Alongside the speedy developments in digital technology, visuals depicting the up-to-date electronics , artificial intelligence , and innovations are in great demand .
Diversity Multiplicity: Display matters , and illustrations recognizing multiplicity and incorporation are extensively respected . Crafting and Arts: With the growth of innovative activities during confinements, handmade handiwork and self-made activities are in demand .
Be Genuine : Truthfulness strikes a chord with audiences . True situations and real emotions often fare better than staged pictures . Top-notch Visuals : Ensure your photos like 8 Reasons SMBs are a Top Target For Cyber Attacks - Network Doctor, Cyber Threats Part 2: Phishing and Spear Phishing Attacks - TSG are first-rate definition and properly lit . Poor sharpness illustrations frequently do take away from your content .
Appropriate Keywords : Apply fitting hashtags to boost exposure . Explore trending keywords in your industry . Cohesive Presence : Maintain a unchanging theme and color to reinforce your brand persona . Connect with Existing Situations : Integrate your information to latest developments or crazes to keep applicable .
Keeping up with in vogue photos is crucial for everyone seeking to continue a powerful place in the digital space . By being aware of whom seizes interest and the approach to produce compelling images , you can persist at the forefront of the competition . Initiate testing with the above-mentioned advice and witness your engagement grow ! Acknowledge you for taking in! Be tuned for greater knowledge on current themes and methods to enhance your internet presence .
On other words caring about DNSFilter: Assigning Cybersecurity Responsibility After a Cyberattack you've landed to the right web. We have 15 Pictures about DNSFilter: Assigning Cybersecurity Responsibility After a Cyberattack highlights like 8 Reasons SMBs are a Top Target For Cyber Attacks - Network Doctor, Cyber Threats Part 2: Phishing and Spear Phishing Attacks - TSG and additionally Types of Cyber Attacks. Here it is:
DNSFilter: Assigning Cybersecurity Responsibility After A Cyberattack
 www.dnsfilter.com
www.dnsfilter.com Why Do Cyber Attacks Seem So Widespread? | P&N
 www.pncpa.com
www.pncpa.com cyber attacks do attack why seem widespread so
B&K Issues Cyber-Attack Notice - Infosecurity Magazine
 www.infosecurity-magazine.com
www.infosecurity-magazine.com Cyber Threats Part 2: Phishing And Spear Phishing Attacks - TSG
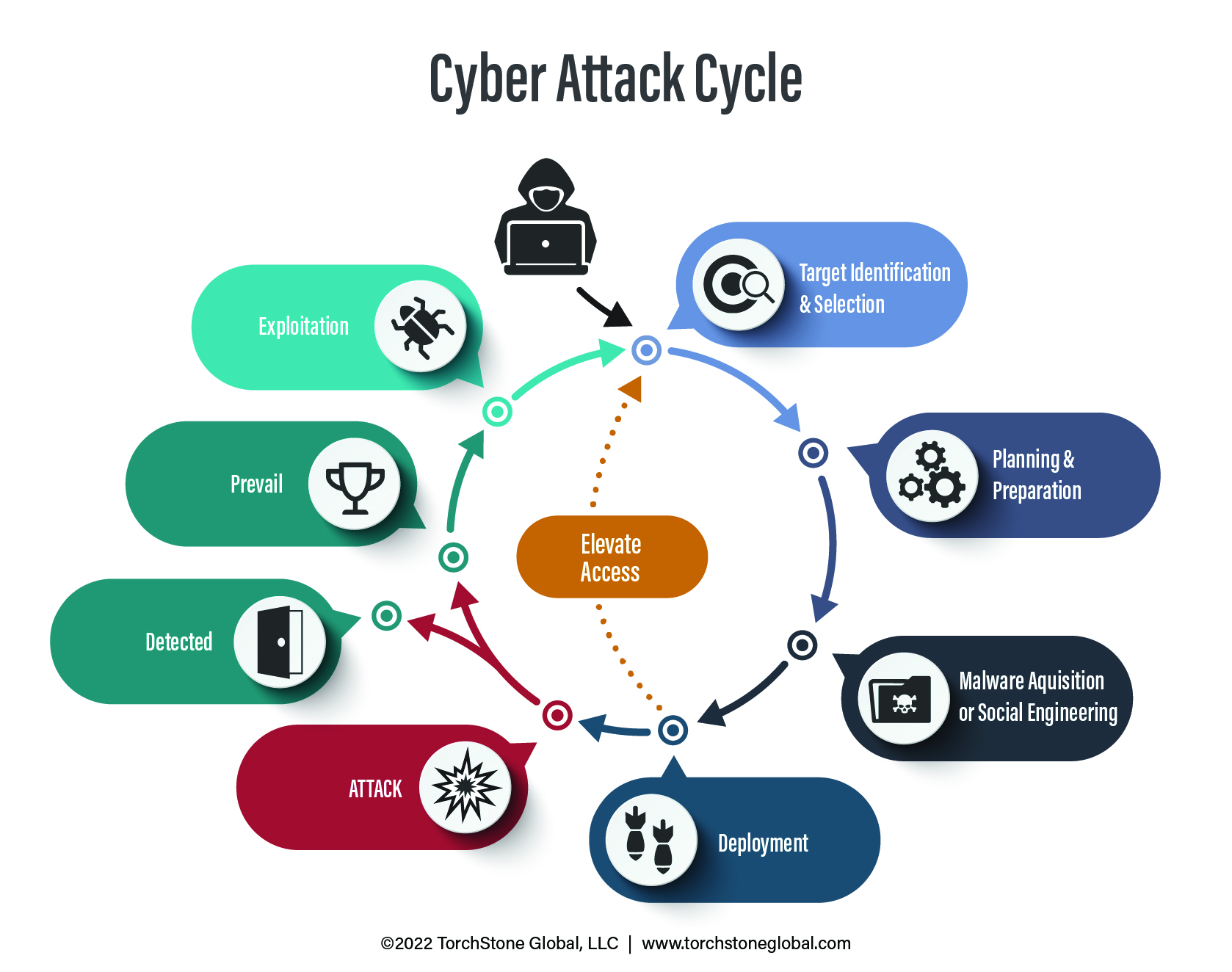 www.torchstoneglobal.com
www.torchstoneglobal.com Moody’s RMS To Invest ‘full Guns Blazing’ In Cyber As Market Reaches
 www.globalreinsurance.com
www.globalreinsurance.com Types Of Cyber Attacks
 cyberandprivacylawyer.blogspot.com
cyberandprivacylawyer.blogspot.com 8 Reasons SMBs Are A Top Target For Cyber Attacks - Network Doctor
 www.networkdr.com
www.networkdr.com Cyberattack Targets PN-G ISD | KFDM
cyberattack
Demystifying Cybersecurity | CDK Global
 www.cdkglobal.com
www.cdkglobal.com Cyberattack On Titan : R/attackontitan
 www.reddit.com
www.reddit.com Hacker Activity Big Set Hacking Computer Phishing Account Cyber Attack
 www.istockphoto.com
www.istockphoto.com 5 Signs A Cyberattack Is Under Way And 5 Things You Need To Do Before
 adamlevin.com
adamlevin.com attacks attack ddos denial service cyberattack stop happens cyber signs under need way before things do increase preventing tips them
Symbol Für Cyberangriffslinie Ransomwarebedrohungszeichen Vektor Stock
Why Manufacturers Need To Be Prepared For A Cyberattack
 www.thefabricator.com
www.thefabricator.com Cyber Attack Or Computer Crime Hacking Password On A Dark Background
 www.stratospherenetworks.com
www.stratospherenetworks.com cyber crime attack computer background hacking dark cybercrime password threat size cybercriminal
Why do cyber attacks seem so widespread?. Attacks attack ddos denial service cyberattack stop happens cyber signs under need way before things do increase preventing tips them. Cyber attacks do attack why seem widespread so
Comments
Post a Comment